Introduction
In today's digital landscape, businesses face an ever-evolving threat of cyber attacks. Cyber security has become a critical concern for organizations of all sizes, as the consequences of a successful breach can be devastating, leading to financial losses, reputational damage, and regulatory compliance issues. Effective business process modeling is crucial in ensuring a robust and efficient response to cyber security events.
According to a recent study by the Ponemon Institute, the global average cost of a data breach in 2022 was $4.35 million, a 2.6% increase from the previous year. With the increasing frequency and sophistication of cyber threats, it is essential for businesses to have a well-defined and well-documented process for responding to such events.
Understanding the Cyber Security Event Response Process
The cyber security event response process is a structured approach to identifying, containing, and resolving security incidents. This process typically involves several key steps, including:
- Identification: Detecting and recognizing a potential cyber security event, such as a data breach, malware infection, or unauthorized access.
- Containment: Taking immediate actions to limit the impact of the event and prevent further damage.
- Eradication: Removing the root cause of the event, such as eliminating the source of the malware or closing the security vulnerability.
- Recovery: Restoring normal business operations and ensuring that the affected systems and data are fully restored.
- Lessons Learned: Reviewing the incident and identifying areas for improvement in the cyber security event response process.
Effective business process modeling can help organizations streamline and optimize each of these steps, ensuring a more coordinated and efficient response to cyber security events.
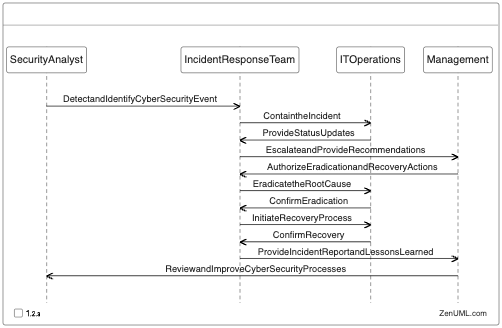
ZenUML Sequence Diagram: Cyber Security Event Response Process
To better visualize the cyber security event response process, let's use a ZenUML sequence diagram:
Key Components of Effective Business Process Modeling
To ensure a comprehensive and effective response to cyber security events, businesses should consider the following key components in their business process modeling:
-
Clearly Defined Roles and Responsibilities: Establish clear roles and responsibilities for each team member involved in the cyber security event response process, ensuring seamless coordination and accountability.
-
Incident Response Plan: Develop a detailed incident response plan that outlines the step-by-step procedures for identifying, containing, eradicating, and recovering from a cyber security event.
-
Communication and Escalation Protocols: Implement effective communication and escalation protocols to ensure that relevant stakeholders are informed and involved in the decision-making process throughout the incident response.
-
Automated Incident Detection and Reporting: Leverage technology solutions, such as security information and event management (SIEM) systems, to automate the detection and reporting of cyber security events, enabling a more timely and efficient response.
-
Continuous Improvement: Regularly review and update the cyber security event response process, incorporating lessons learned from previous incidents and incorporating best practices to enhance the organization's overall cyber resilience.
Integrating Business Process Modeling into Cyber Security Strategies
Effective business process modeling for cyber security event response should be an integral part of an organization's overall cyber security strategy. By aligning the incident response process with the broader cyber security framework, businesses can ensure a more holistic and effective approach to managing cyber threats.
This integration can include the following elements:
-
Risk Assessment and Mitigation: Incorporate the cyber security event response process into the organization's risk assessment and mitigation activities, ensuring that potential vulnerabilities and threats are identified and addressed.
-
Incident Response Drills and Tabletop Exercises: Regularly conduct incident response drills and tabletop exercises to test the effectiveness of the cyber security event response process and identify areas for improvement.
-
Employee Training and Awareness: Provide comprehensive training and awareness programs to ensure that all employees understand their roles and responsibilities in the event of a cyber security incident.
-
Vendor and Third-Party Management: Extend the cyber security event response process to include the management of vendors and third-party service providers, who may also be impacted by or involved in the incident.
-
Regulatory Compliance: Ensure that the cyber security event response process aligns with relevant regulatory requirements, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA).
Conclusion
In today's rapidly evolving cyber threat landscape, effective business process modeling for responding to cyber security events is crucial for organizations of all sizes. By leveraging tools like ZenUML sequence diagrams and incorporating key components of effective incident response, businesses can enhance their overall cyber resilience and better protect their critical assets.
As you continue to refine and improve your cyber security event response process, we encourage you to share your insights and experiences in the comments section below. Your feedback and contributions can help shape the best practices and strategies for businesses navigating the complex world of cyber security.
Try ZenUML now!
Zenuml detailed feature roadmap available here.